Microsoft defender will sometimes block TDO from creating child processes. Child processes are important to using TDO as they are required to use various TDO modules such as electronic prescriptions, letters, and auto fix. This Microsoft article outlines how to provide exclusions so that the processes will not be blocked.
Use Group Policy to exclude files and folders
On your Group Policy management computer, open the Group Policy Management Console, right-click the Group Policy Object you want to configure and select Edit.
In the Group Policy Management Editor, go to Computer configuration and click Administrative templates.

Expand the tree to Windows components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Attack surface reduction.
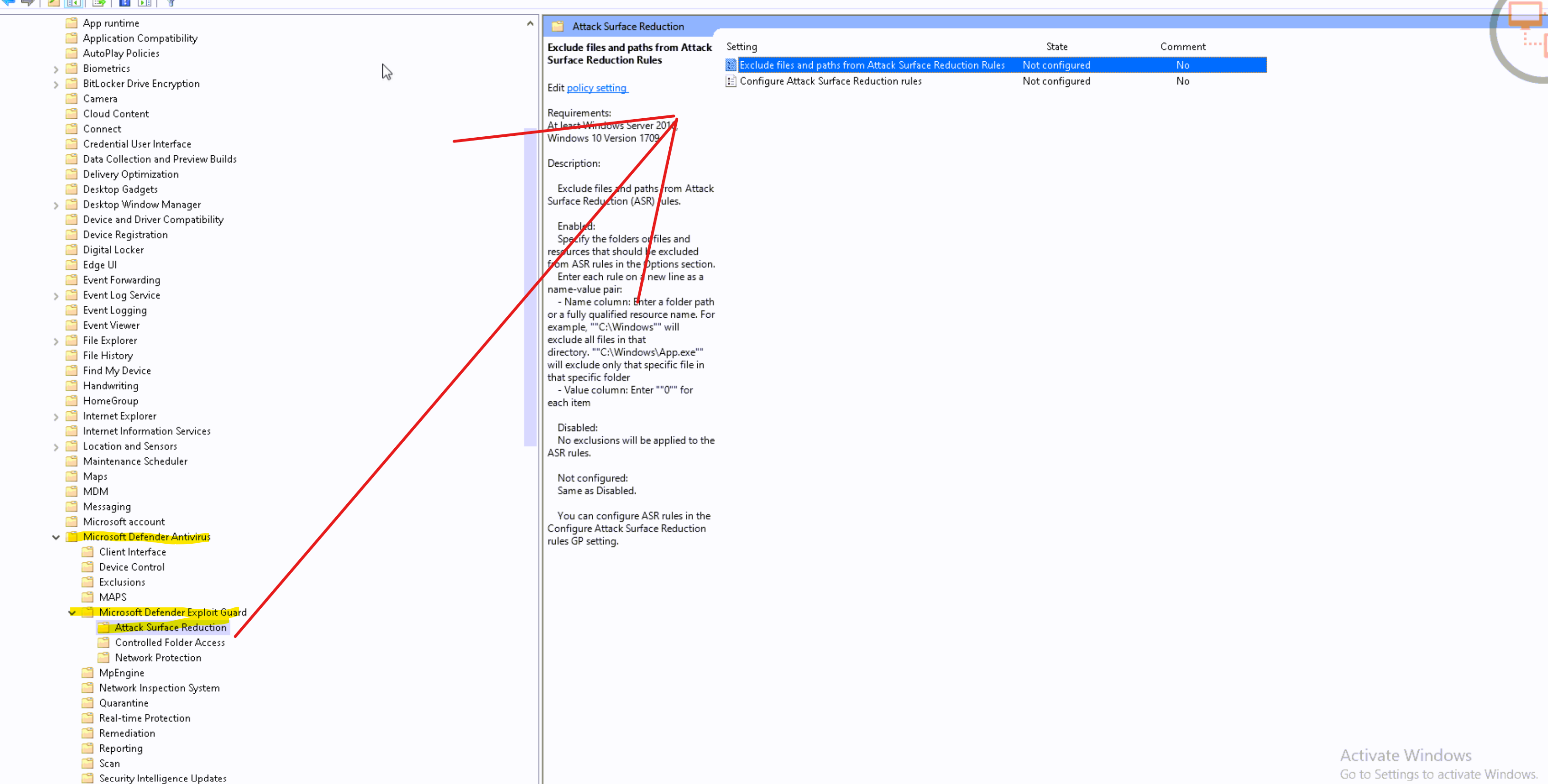
Double-click the Exclude files and paths from Attack surface reduction Rules setting and set the option to Enabled. Select Show and enter each file or folder in the Value name column. Enter 0 in the Value column for each item.
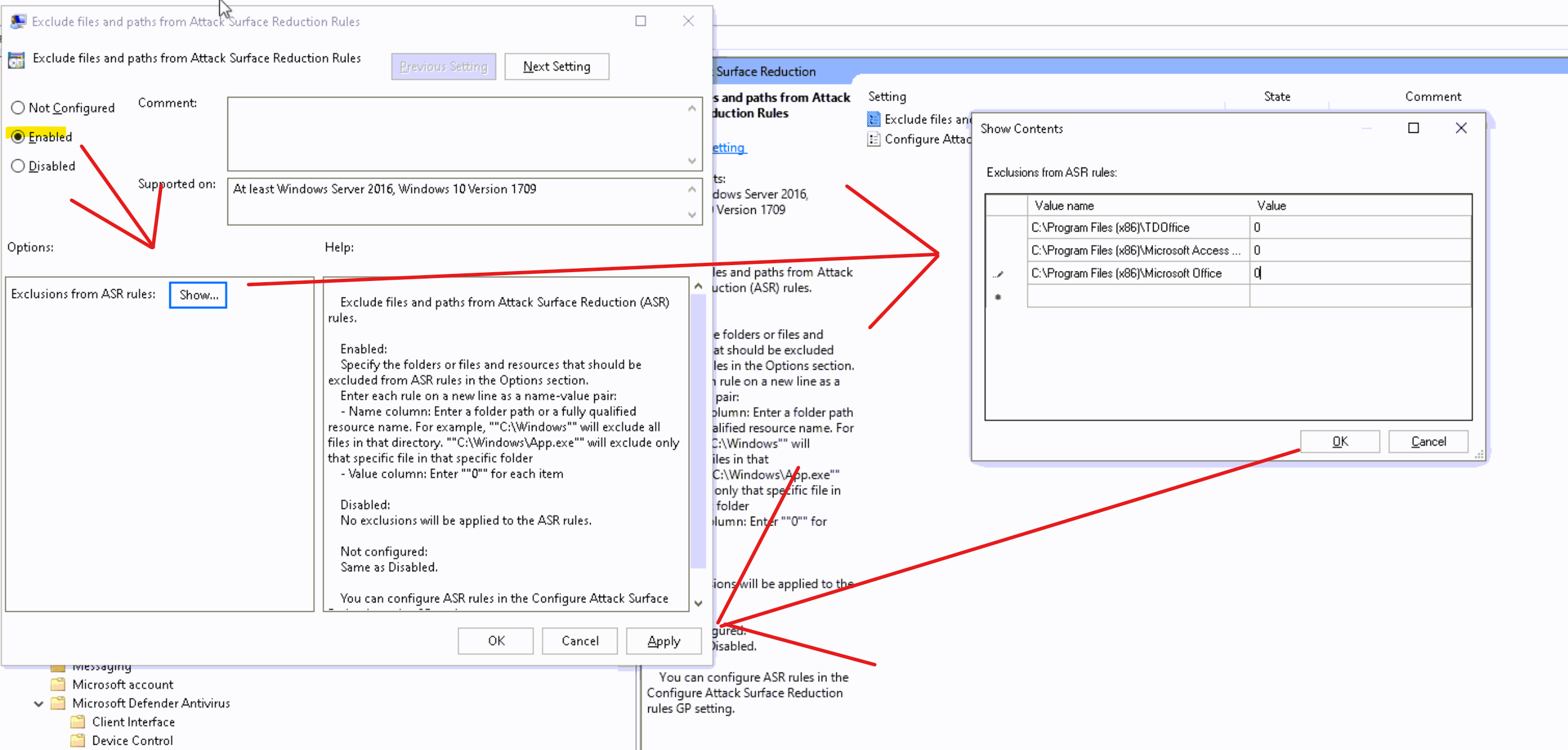
Paths to add:
64bit Workstations
If using RVG Kodak Integration:
Article ID: 960
Created: January 24, 2024
Last Updated: July 21, 2025
Author: TDO KB [web_admin@tdo4endo.com]
Online URL: https://kb.tdo4endo.com/article.php?id=960